How To Fix Remote IoT Platform SSH Key Not Working: A Comprehensive Guide
Are you facing issues with your remote IoT platform SSH key not working? This problem can be frustrating, especially when you rely on secure connections to manage your IoT devices. Whether you're a developer, system administrator, or IoT enthusiast, troubleshooting SSH key issues is critical to maintaining seamless operations. In this guide, we’ll walk you through the possible causes of this issue and provide actionable solutions to resolve it.
SSH (Secure Shell) is a protocol widely used for secure remote access to IoT platforms. It ensures encrypted communication between your local machine and remote servers. However, when SSH keys fail to authenticate, it disrupts workflows and compromises security. Understanding the root cause of the problem is the first step toward resolution.
In this article, we’ll explore the common reasons why SSH keys may not work on remote IoT platforms, step-by-step troubleshooting methods, and best practices to prevent future occurrences. By the end of this guide, you’ll have a clear understanding of how to address this issue and ensure your IoT platform remains secure and functional.
Read also:Understanding Bo Basset Weight A Comprehensive Guide
Table of Contents
- Understanding SSH Keys and Their Role in IoT Platforms
- Common Causes of Remote IoT Platform SSH Key Not Working
- Step-by-Step Troubleshooting for SSH Key Issues
- Best Practices for Managing SSH Keys on IoT Platforms
- Advanced Solutions for Persistent SSH Key Issues
- Tools and Resources for SSH Key Management
- Real-World Examples of SSH Key Failures
- Security Considerations When Using SSH Keys
- Conclusion and Next Steps
Understanding SSH Keys and Their Role in IoT Platforms
SSH keys are a pair of cryptographic keys used to authenticate users and devices in a secure manner. They consist of a private key, which is kept on the user's local machine, and a public key, which is stored on the remote server or IoT platform. When configured correctly, SSH keys eliminate the need for password-based authentication, reducing the risk of brute-force attacks.
In the context of IoT platforms, SSH keys are essential for managing devices remotely. They enable secure communication between IoT devices and centralized servers, ensuring data integrity and confidentiality. Without proper SSH key management, IoT platforms become vulnerable to unauthorized access and potential breaches.
Understanding how SSH keys work is crucial for diagnosing and resolving issues. If your remote IoT platform SSH key is not working, it could stem from misconfigurations, corrupted files, or incorrect permissions. Let’s explore the common causes of this problem in the next section.
Common Causes of Remote IoT Platform SSH Key Not Working
When troubleshooting SSH key issues, it’s important to identify the root cause. Below are some of the most common reasons why your remote IoT platform SSH key may not be working:
- Incorrect File Permissions: SSH is highly sensitive to file permissions. If the private key or authorized_keys file has incorrect permissions, the SSH client may reject the key.
- Corrupted or Missing Keys: If the private or public key is corrupted or deleted, the authentication process will fail.
- Wrong Key Format: SSH keys must be in the correct format (e.g., RSA, ECDSA, or Ed25519). Using an incompatible format can lead to authentication errors.
- Server Configuration Issues: The SSH server on the IoT platform may be misconfigured, preventing it from accepting key-based authentication.
- Network or Firewall Restrictions: Firewalls or network policies may block SSH traffic, preventing the connection from being established.
By understanding these potential causes, you can systematically troubleshoot and resolve the issue. In the next section, we’ll provide a step-by-step guide to help you diagnose and fix the problem.
Step-by-Step Troubleshooting for SSH Key Issues
Resolving SSH key issues requires a methodical approach. Follow the steps below to identify and fix the problem with your remote IoT platform SSH key not working.
Read also:177013 Lego Exploring The Intricate World Of Lego Sets
Check File Permissions
SSH is strict about file permissions to ensure security. Incorrect permissions can cause authentication failures. Follow these steps to verify and correct file permissions:
- Ensure the private key file has permissions set to 600 (read and write for the owner only).
- Verify that the authorized_keys file on the server has permissions set to 644 (read and write for the owner, read-only for others).
- Check the .ssh directory permissions, which should be set to 700 (read, write, and execute for the owner only).
To modify permissions, use the following commands:
chmod 600 ~/.ssh/id_rsa chmod 644 ~/.ssh/authorized_keys chmod 700 ~/.sshVerify SSH Key Format
SSH keys must be in the correct format to work properly. If you’re using an outdated or incompatible key format, authentication will fail. Follow these steps to verify and convert your SSH key format:
- Check the key format by opening the private key file. It should begin with "-----BEGIN RSA PRIVATE KEY-----" or a similar header.
- If the key is in an older format, use the ssh-keygen tool to convert it:
ssh-keygen -p -m PEM -f ~/.ssh/id_rsaTest the SSH Connection
Once you’ve addressed potential issues with permissions and key format, test the SSH connection to ensure everything is working correctly:
- Use the following command to test the connection:
ssh -v user@remote-iot-platformThe -v flag provides verbose output, helping you identify any remaining issues. Look for error messages related to authentication or key exchange.
Best Practices for Managing SSH Keys on IoT Platforms
To prevent SSH key issues in the future, it’s important to follow best practices for key management. Below are some recommendations:
- Regularly Rotate Keys: Periodically generate new SSH key pairs to reduce the risk of compromise.
- Use Strong Passphrases: Protect your private key with a strong passphrase to add an extra layer of security.
- Limit Key Usage: Restrict SSH keys to specific users or devices to minimize exposure.
- Monitor Key Activity: Use logging and monitoring tools to track SSH key usage and detect anomalies.
By implementing these practices, you can ensure the security and reliability of your remote IoT platform SSH connections.
Advanced Solutions for Persistent SSH Key Issues
If basic troubleshooting steps fail to resolve the issue, consider implementing advanced solutions:
- Reconfigure the SSH Server: Check the SSH server configuration file (usually located at /etc/ssh/sshd_config) and ensure key-based authentication is enabled.
- Update SSH Software: Ensure both the client and server are running the latest version of the SSH software to avoid compatibility issues.
- Use a Key Management Tool: Tools like HashiCorp Vault or AWS Key Management Service can help manage SSH keys securely and efficiently.
Tools and Resources for SSH Key Management
Managing SSH keys effectively requires the right tools and resources. Below are some recommended options:
- ssh-keygen: A built-in tool for generating and managing SSH keys.
- OpenSSH: The most widely used SSH implementation, offering robust features for secure connections.
- HashiCorp Vault: A tool for securely storing and managing SSH keys.
These tools can streamline key management and enhance the security of your IoT platform.
Real-World Examples of SSH Key Failures
To illustrate the importance of proper SSH key management, consider the following real-world scenarios:
- Case Study 1: A company experienced a security breach due to improperly configured SSH keys, leading to unauthorized access to their IoT devices.
- Case Study 2: A developer spent hours troubleshooting an SSH key issue caused by incorrect file permissions, highlighting the need for attention to detail.
These examples underscore the importance of following best practices and addressing issues promptly.
Security Considerations When Using SSH Keys
SSH keys are a powerful tool, but they must be used responsibly to ensure security. Below are some key considerations:
- Avoid Hardcoding Keys: Never hardcode SSH keys into scripts or applications, as this increases the risk of exposure.
- Enable Multi-Factor Authentication: Combine SSH key authentication with MFA for added security.
- Regularly Audit Keys: Periodically review and audit SSH keys to ensure they are still necessary and secure.
By prioritizing security, you can protect your IoT platform from potential threats.
Conclusion and Next Steps
In this comprehensive guide, we’ve explored the common causes of remote IoT platform SSH key not working and provided actionable solutions to resolve the issue. From checking file permissions to implementing advanced tools, these steps will help you restore secure connections and prevent future problems.
Now it’s your turn to take action. Test the troubleshooting steps outlined in this guide and implement best practices to ensure the security of your IoT platform. If you found this article helpful, share it with others who may benefit from it. For more resources on IoT security and SSH management, explore our other articles on the topic.
Best Remote Access IoT Devices Free: A Comprehensive Guide To Secure And Efficient Connectivity
How To Set Up Remote SSH Access To Raspberry Pi: A Comprehensive Guide
Vega Move NL: The Ultimate Guide To Sustainable Urban Mobility
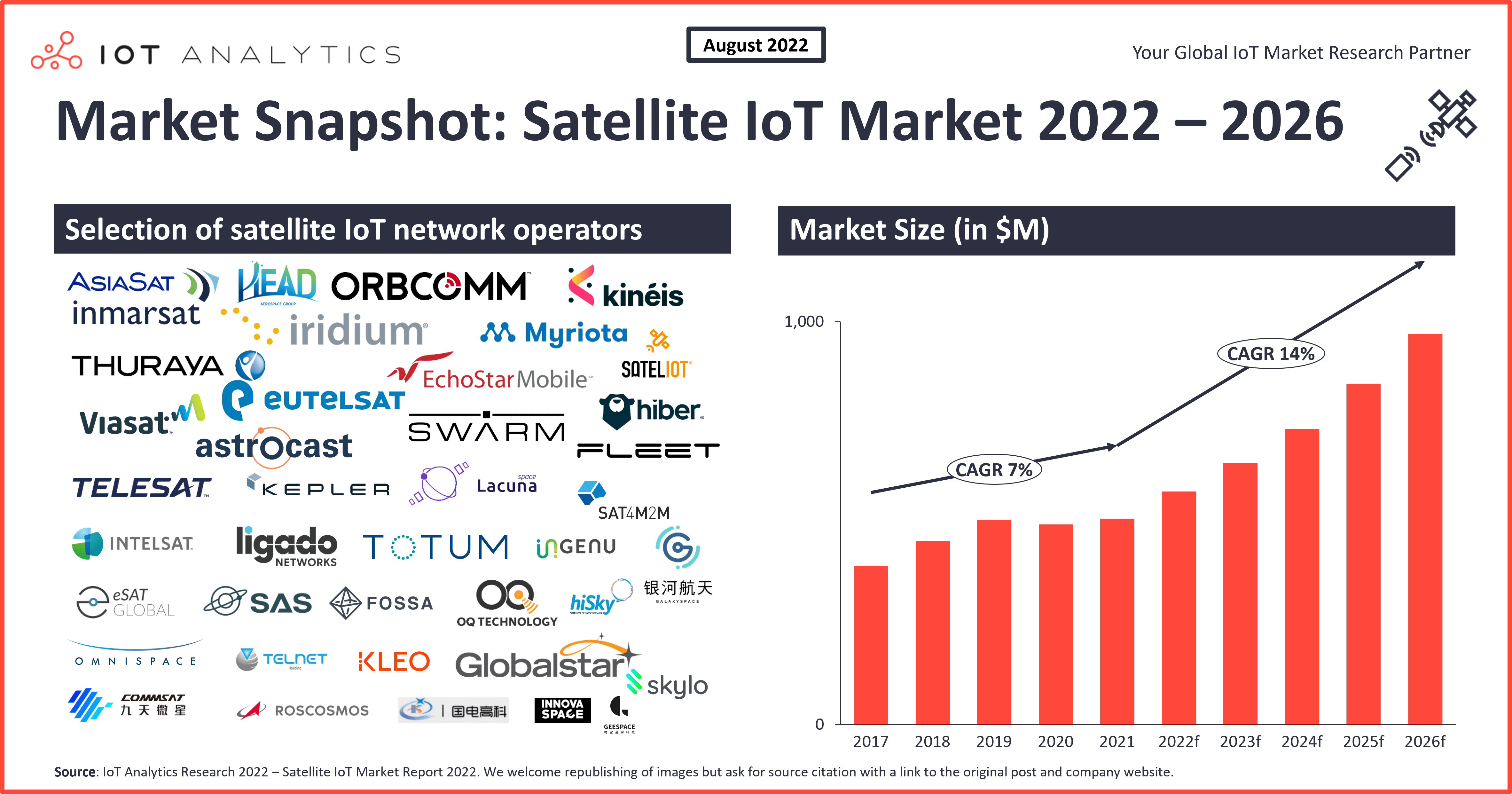
Satellite IoT connectivity Three key developments to drive the market
The leading IoT software companies 2023